Rooting Kioptrix: Level 1
This vulnerable VM, available from Vulnhub here, was a fairly easy one to crack, and is reminiscent of some of the easier machines in the PWK/OSCP online labs. To get started, download it and fire it up in VirtualBox, or whatever hypervisor you like, along with your attack machine.
Host Discovery
Now that the VM is up and running, we need to discover its IP address in our virtual network (which should obviously be host-only or internal). A ping-sweep tool such as fping or nmap -sn will do the trick.
I'm 192.168.56.1, so our target is at 192.168.56.103. Now we start enumeration of our victim. First, we'll do a basic nmap version detection scan of the target machine:
From this, we can see that this is running an Apache webserver, an OpenSSH server, and some version of Samba. Let's do a more in depth enumeration using enum4linux:
Enum4linux can provide copious amounts of sometimes hard to digest data, but the important bit to note here is that it often discovers the exact version information of a Samba server, as seen below:
Enum4linux tells us that our target is running Samba 2.2.1a. Immediately this raises red flags, as the versions of Samba in the 2.2.x range are notorious for their vulnerabilities. Let's use searchsploit to see if our version matches any known exploits available in Kali.
Quick note on searchsploit usage: If a search for the specific version doesn't return many results, make your search progressively more vague, to see if any of those results match the target software.
As we can see, there are many results for Samba 2.2.x exploits, utilizing the trans2 vulnerability. Many of these could be effective, but I'm going to try the one named 10.c. Note that the version listed by searchsploit, 2.8, doesn't match our own. This is an error, as we can see when we actually look at the file:
This is an old exploit called sambal.c that utilizes the vulnerable trans2open call to (hopefully) gain root access on our target server. If you wish to read more about this exploit, the underlying trans2 vulnerability, and a whole lot more about Samba, SANS has a great paper on the topic. (Pay no attention, however, to the part that says the connectback shellcode in the sambal.c exploit contains an incorrect offset and must be fixed. This is not the case, as will soon be made evident.)
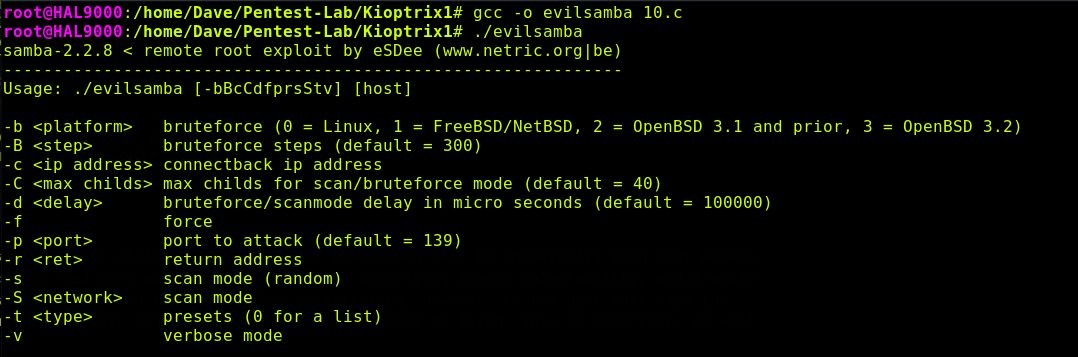
Moving on, let's compile the exploit and look at its usage data:
As our target seems to be running Red Hat Linux, let's run the exploit with the Linux platform selected:
Root! At this point, we could copy over the shadow and passwd files to crack the password hashes, view any other files on the server, or do pretty much anything else we want. The "flag" for us to capture is actually in the /var/mail directory, here:
There you have it. Stay tuned for the next one.
Host Discovery
Now that the VM is up and running, we need to discover its IP address in our virtual network (which should obviously be host-only or internal). A ping-sweep tool such as fping or nmap -sn will do the trick.
I'm 192.168.56.1, so our target is at 192.168.56.103. Now we start enumeration of our victim. First, we'll do a basic nmap version detection scan of the target machine:
From this, we can see that this is running an Apache webserver, an OpenSSH server, and some version of Samba. Let's do a more in depth enumeration using enum4linux:
Enum4linux can provide copious amounts of sometimes hard to digest data, but the important bit to note here is that it often discovers the exact version information of a Samba server, as seen below:
Enum4linux tells us that our target is running Samba 2.2.1a. Immediately this raises red flags, as the versions of Samba in the 2.2.x range are notorious for their vulnerabilities. Let's use searchsploit to see if our version matches any known exploits available in Kali.
Quick note on searchsploit usage: If a search for the specific version doesn't return many results, make your search progressively more vague, to see if any of those results match the target software.
As we can see, there are many results for Samba 2.2.x exploits, utilizing the trans2 vulnerability. Many of these could be effective, but I'm going to try the one named 10.c. Note that the version listed by searchsploit, 2.8, doesn't match our own. This is an error, as we can see when we actually look at the file:
This is an old exploit called sambal.c that utilizes the vulnerable trans2open call to (hopefully) gain root access on our target server. If you wish to read more about this exploit, the underlying trans2 vulnerability, and a whole lot more about Samba, SANS has a great paper on the topic. (Pay no attention, however, to the part that says the connectback shellcode in the sambal.c exploit contains an incorrect offset and must be fixed. This is not the case, as will soon be made evident.)
Moving on, let's compile the exploit and look at its usage data:
As our target seems to be running Red Hat Linux, let's run the exploit with the Linux platform selected:
Root! At this point, we could copy over the shadow and passwd files to crack the password hashes, view any other files on the server, or do pretty much anything else we want. The "flag" for us to capture is actually in the /var/mail directory, here:
There you have it. Stay tuned for the next one.










Comments
Post a Comment